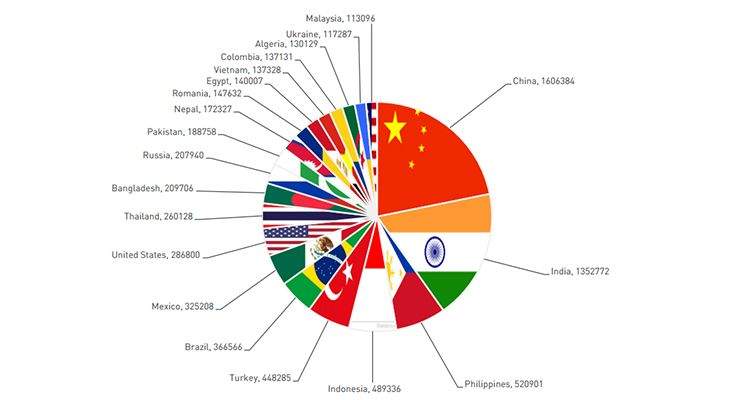
Big Tech, Politics, and Scandals
When Christopher Wylie was in his mid-teens, he expressed hopes of becoming a statesman. If not, he assumed he would be another small merchant resorting to Machiavellian methods to sell petty goods. A decade later, he finds a place in the list … Read More