Keylogger : A potential threat camouflaged behind innocence !!

Keylogger : A potential threat camouflaged behind innocence !!
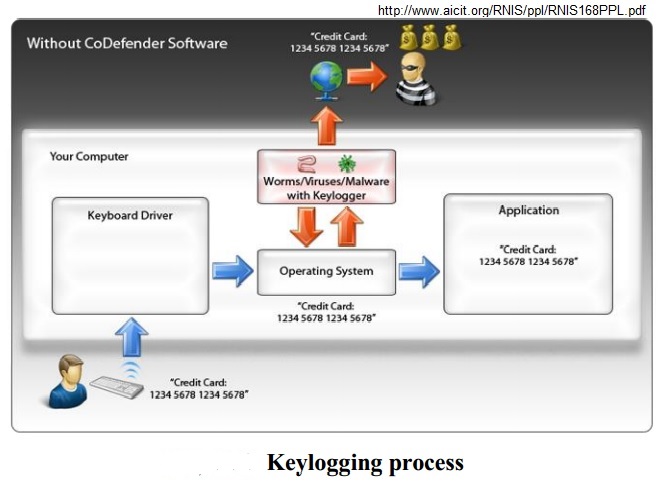
Ever thought what it would be like if someone gets details of every tap you make on the keyboard? You will be exposed way beyond your comfort level. All your data, be it private or public, will be in the hands of someone you do not fancy. Yes, that’s the power of a keylogger and the level to which they have advanced, definitely pose a serious threat. The newer keyloggers can extract so much information that it is not even funny. Some of them can even tap your camera and microphone for “TOTAL MONITORING DOMINATION”,
For those of who do not know, keylogger is software or a device that monitors and creates a log of every keystroke thus compromising with your information security. Some keyloggers even take screen shots from time to time keeping a track of your activity. These images and data are then sent to the person who is registered to get the details. Like any other software or device it’s a good tool put to bad use. Originally, key logger was designed to keep a track of employees at work, keep a track of your personal system to prevent any misuse etc. The enormous potential of the Internet has therefore led to an increase in keylogging attempts. The easy availability of key loggers in market made them a weapon of crime and the fact that even script-kiddies can make one is just an add on factor.
Key loggers have root kit functionality which helps them hide in the system in the form of full-fledged Trojan programs. A fundamental concept behind keyloggers and similar malware is their pattern of attack. Most malware infections follow a fairly standard attack pattern that involves the sequential order of development, distribution and infection, and execution stages. The initial phase is vital to the process as any malware that is not yet implemented cannot be used by an attacker. What is unique about the development stage is that it places emphasis on how the latter stages will be accomplished. Distribution and execution can both be implemented as a component of the malware and therefore are a contribution factor in its design and development.
Study by Provos et al.[i] shows that there are four distinct approaches to malware placement on the Internet for distribution:
1) Advertisements. These provide a common hosting place for malware. As advertisements often tend to be redirections chained together, it is possible for thirdparties to inject the location of malicious content into one of the nodes in the chain.
2) Third-party widgets. As with advertisements, widgets are fundamentally embedded links, often to an external Javascript function or similar entities, that can be redirected to dangerous locations.
3) User contributed content. Here a typical web user physically uploads content to a public location. If the web master does an inadequate job of checking content legality and validity via appropriate sanitization techniques, malicious content placement may occur.
4) Web server security mechanisms. These mechanisms also play an important role as they can impede malware placement on web sites by controlling server content such as HTML, Javascript, PHP (or other scripting languages and applications), and database contents. Therefore, an attacker who gains control of these security mechanisms has the ability to completely control the content on the web server and use it to her advantage.
Studies show, that key logger has pushed back phishing to take the first spot in methods used by cyber criminals. History has witnessed a number of dangerous keylogger attacks.
On January 24, 2004 the notorious Mydoom worm caused a major epidemic. MyDoom broke the record previously set by Sobig, provoking the largest epidemic in Internet history to date. The worm used social engineering methods and organized a DoS attack on www.sco.com; the site was either unreachable or unstable for several months as a consequence. The worm left a Trojan on infected computers which was subsequently used to infect the victim machines with new modifications of the worm. The fact that MyDoom had a keylogging function to harvest credit card numbers was not widely publicized in the media.
One of the most publicized keylogging incidents recently was the theft of over $1million from client accounts at the major Scandinavian bank Nordea. In August 2006 Nordea clients started to receive emails, allegedly from the bank, suggesting that they install an antispam product, which was supposedly attached to the message. When a user opened the file and downloaded it to his/ her computer, the machine would be infected with a well known Trojan called Haxdoor. This would be activated when the victim registered at Nordea’s online service, and the Trojan would display an error notification with a request to re-enter the registration information. The keylogger incorporated in the Trojan would record data entered by the bank’s clients, and later send this data to the cyber criminals’ server. This was how cyber criminals were able to access client accounts, and transfer money from them. According to Haxdoor’s author, the Trojan has also been used in attacks against Australian banks and many others.[ii]
News dated 13th January 2015 featuring keysweeper, a 10$ USB device with built in wireless keylogger, on zdnet.com would have definitely sent shivers through ones spine.
“On the outside it looks like a regular wall wart, but on the inside is an Arduino microcontroller that allows the KeySweeper to connect to nearby wireless keyboards and passively sniff, decrypt and log all of the keystrokes. These keystrokes are then transmitted over the Internet using an optional GSM module, or stored on flash memory inside the device. Unplugging KeySweeper doesn’t make you any safer either because it also features an internal battery.This device is possible because of the painfully weak security employed by wireless keyboards. Defending against it is a challenge in itself for security researchers.”[iii]
Security is a concern for everybody. The anti-virus softwares now available in the market can easily detect the presence of a key logger on your system. The static nature of keyloggers makes it easy for antimalware softwares to detect them. There are a number of simple you can observe if you have suspects that your system has a keylogger.
- Anti-virus:
The antivirus softwares available today can easily detect a keylogger if any on your system.
- Task List:
Check you task list (CTRL + ALT + DEL) to see what all programs are running and check for any suspicious program.
- Hard disk:
Check your hard disk for most recent files stored. Look at contents of any files that update often as they might be logs.
- Msgconfig:
Type “msconfig”in your run box to access the list and check what all programs are loaded at computer start-up.
- OTP:
Make use of one time passwords as they change for online transaction wherever possible.
- Virtual keyboard:
Virtual keyboards are beneficial and safe when the keylogger is not programed to click screen shots.
Also make sure you never use a system at cyber café or someone else’s system in general for making transactions or accessing private emails etc. because the system might have a keylogger and you would be giving away your data. When keylogger detection and prevention techniques are inadequate in terms of capability or performance, user applications can simply avoid keyboard input by using alternatives for user input. A simple alternative is the use of automatic form fillers for web browsers; not needing to type in sensitive information each time a specific web page is visited reduces the leaking of private data. Another alternative is to use a different input mechanism; for example, audio input and appropriate speech recognition software could effectively foil a running keylogger.
We can thus say, the power of keylogger should not be under estimated. It is working as a silent killer just camouflaged below a skin of simplicity and innocence.
[i] N. Provos, D. McNamee, P. Mavrommatis, K. Wang, and N. Modadugu, “The ghost in the browser analysis of web-based malware,” in HotBots’07: Proceedings of the first conference on First Workshop on Hot Topics in Understanding Botnets. Berkeley, CA, USA: USENIX Association, 2007, pp. 4–4
[ii] https://securelist.com/analysis/36138/keyloggers-how-they-work-and-how-to-detect-them-part-1/
[iii] http://www.zdnet.com/article/a-10-usb-charger-with-built-in-wireless-keylogger-is-a-security-nightmare/
You can read more on this from our friends at Cyber Cops here: 3 Easy Way to Detect if Keylogger is Installed in Windows-10