Smart watches and Heaps of Threats

Ever fancied owning a smartwatch? Or do you own one? Well, you might be stunned after knowing that these wearable devices pose a lot of security risks. Smart watches, smart bands, and even wireless panels can pose a threat to your online identity. Moreover, these are devices gaining remote access to the stuff in your smartphones or computers, referred to as IoT (Internet of Things) devices. However, according to HP, they don’t provide the same level of security.
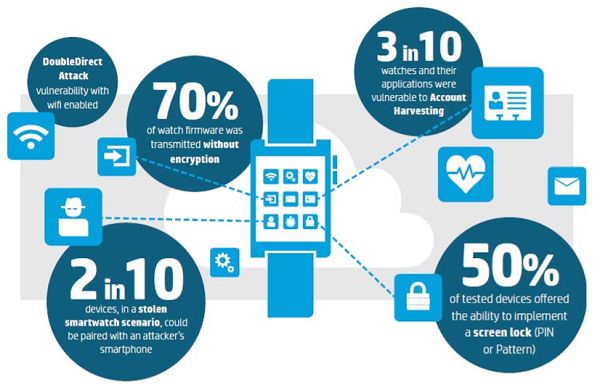
HP did an assessment of 10 different smartwatches and smart bands having different specifications, along with their respective mobile and computer applications. Subsequently, they found out that each one of them had some issues that could make it vulnerable. Every smartwatch collects personal data including name, date of birth, location etc, but none of them has an effective way to keep this information secure. 90% of the cases display that the information retrieved from a smartwatch is easy to intercept. Furthermore, more than 40% of these smartwatches have firmware that can easily leak away the information, the study suggested.
Smartwatches and other wearables primarily pose the risk at two levels, which are as follows:
- Device level: Most of the smartwatches tested by HP had various insecurities related to the device’s firmware. None of the devices had a two-factor authentication, or the ability to lock the device after a number of failed attempts.
- Transit level: At the transport layer, while transmitting the data between the host device and the smartwatch, the assessed smartwatches lacked a strong cypher. In four out of ten cases, they could easily decipher the encryption of the transmitted data.
“The combination of account enumeration, weak passwords, & lack of account lockout means 30 per cent of watches and their applications were vulnerable to account harvesting, allowing attackers to guess login credentials and gain access to user accounts,” Daniel Miessler, the lead researcher of this study said. He also suggested, “it will be a matter of creating policies for managing IoT and wearables within the enterprise, whether that’s creating isolated segments on the LAN, determining what types of devices and capabilities are allowed in sensitive corporate areas.”