Pretty Good Privacy

PGP stands for Pretty Good Privacy. It is an encryption and decryption standard used widely these days. This post will tell you what exactly a PGP is and how it works. In another post, I will tell you how to set up a PGP. It is also called hybrid cryptography as it uses hashing, data compression, symmetric key and public key cryptography.
What is Pretty Good Privacy?
Developed in 1991 by Phil Zimmerman, PGP is used for encrypting and decrypting texts, emails, directories, files and whole disk partitions. It is implemented in the authentication of digital signatures too.
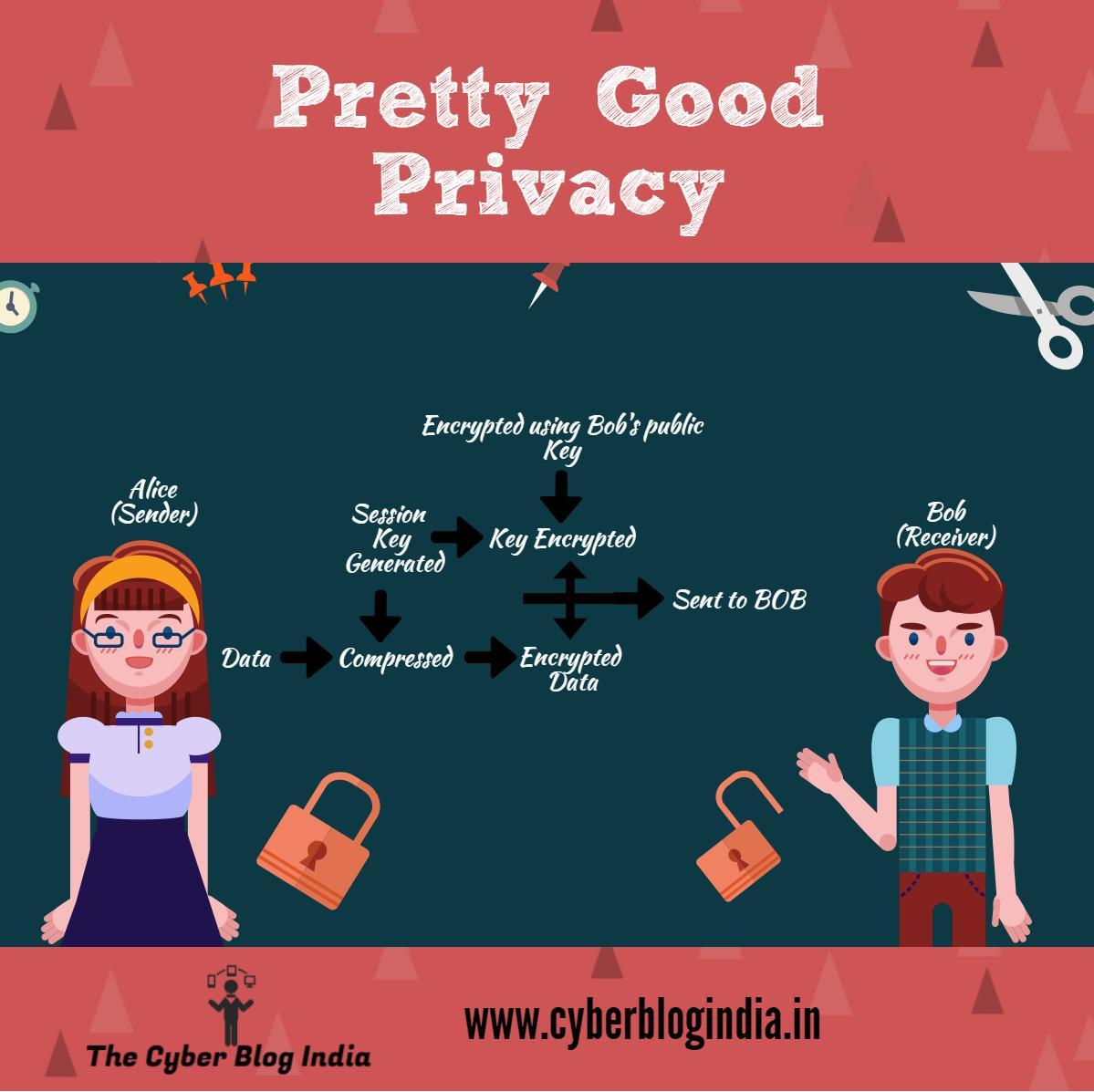
A common question that pops into every human mind is what makes PGP better than others? When a hacker tries to do cryptanalysis[1], he deduces the pattern of the encrypted text. PGP compresses the data making it impossible to study the correct patterns. Compressing the data also reduces the size thus making it easier and faster to transport the data. A session key is generated after this based on your pattern of keyboard and mouse movements. It is a one-time-key and unique to all. This session key encrypts the compressed data. After this, the session key gets encrypted through the RSA algorithm. For this encryption, the receiver’s public key is used. The encrypted data and key are then sent to the receiver. This is the encryption process.
Can I decrypt it?
The decryption is an exactly similar process following a reverse approach. The receiver receives this and uses its private key to decrypt the session key. This session key is then used to decrypt the encrypted ciphertext. The convenience of public key encryption along with the speed of conventional key encryption makes PGP stand out without compromising on security.
PGP was not Open Source due to the presence of a patent. Zimmerman convinced IETFT[2], which soon set an OpenPGP standard and opened an OpenPGP Work Group. Today, several developers and companies developing their unique PGP based on this standard, which is proving beneficial for society.
[1] trying to study the encrypted data
[2]Internet Engineering Task Force