A Beginner’s Guide to Cryptography

Cryptography has been derived from the Greek word kryptos, which means hidden. It involves converting information in a manner that it can only be read and processed by the intended receivers. Crypt means hidden and graphy means writing. One of the earliest instances of cryptography is traced back to the use of Hieroglyph in which scribes used to encode/decode the messages on behalf of the kings. In our ever-evolving cyber space where attacks are getting more and more sophisticated, cryptography is considered as one of the most efficient solutions to minimize the overall security risk.
Main Objectives of Cryptography
Modern cryptography is concerned with four security objectives:
- Confidentiality: Only the expected receiver of an encoded message should be able to decode and retrieve the message contents.
- Integrity: When data is stored or transmitted, it must not be modified. Hashing is a well-known method to check data integrity.
- Authentication: It identifies whether an individual or system is who they are claiming to be.
- Non-repudiation: It ensures that a party cannot deny their signature or the authenticity of the message they sent.
Types of Cryptography
- Symmetric Key Cryptography: In symmetric key cryptography, the sender and receiver use a shared secret (common key) for encryption and decryption of a message. At times, it is also referred to as private or secret-key cryptography. As compared to asymmetry key cryptography, symmetric algorithms are faster. One of the most significant issues in symmetric key systems is the sharing of the common key when a sender and receiver are communicating for the first time. Data Encryption Standard (DES) and Advanced Encryption Standard (AES) are examples of symmetric key systems.
- Asymmetric Key Cryptography: In asymmetric key cryptography, every user has a pair of keys called private key and public key. This pair of keys are mathematically related to each other such that a message encrypted using a receiver’s public key can only be decrypted by the said receiver’s corresponding private key. As the names suggest, public keys can be shared with anybody while the private key shall not be shared with anybody. Also known as public key cryptography, asymmetric algorithms are considered to be more secure than their symmetric counterparts.
Section 2(1)(f) of the Information Technology Act, 2000 defines “asymmetric crypto system” as a system of a secure key pair consisting of a private key for creating a digital signature and a public key to verify the digital signature. Key pair, private key, and public key are defined under Section 2(1)(x), 2(1)(zc), and 2(1)(zd) respectively.
Well-Known Cryptographic Algorithms
1. DES
Data Encryption Standard (DES) is a symmetric algorithm and as we discussed earlier, it uses the same key for encryption and decryption. It is a block cipher algorithm that uses a 64-bit block. This algorithm relies on Feistel structure for encryption and decryption of messages. As the standard DES algorithms can be easily cracked using modern techniques, Double DES and Triple DES algorithms are used at times. They use 112-bit and 168-bit keys, respectively.

DES Algorithm (Source)
2. AES
Advanced Encryption Standard (AES) is another symmetric algorithm that is six times faster than Triple DES. Like DES, AES also uses symmetric block ciphers. AES key size can be 128, 192, or 256 bits. A common application of AES is to prevent man-in-the-middle attack when files are shared over HTTP. As of now, there does not appear to be any computationally feasible ways to crack this algorithm. However, in 2009, it was shown that AES-192 and AES-256 can be broken by attacks that require 2176 and 2119 time, respectively.
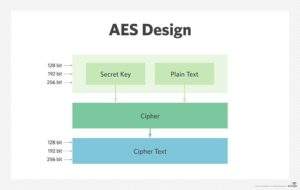
AES Algorithm (Source)
3. RSA
RSA stands for Rivest, Shamir, and Adleman. It is an example of asymmetric cryptography algorithm that was introduced in 1978. The main idea behind RSA is the fact that it is hard to factories a large number. A public key in RSA is calculated by multiplying two prime numbers and similar calculations are done for calculating private key. RSA is commonly used for digital signatures.

RSA Algorithm (Source)
4. Diffie-Hellman
The perfect application of this algorithm is when two parties, that do not previously know each other, have to establish a secure communication channel between themselves. It is difficult to classify this algorithm as either symmetric or asymmetric as it uses key pairs in the key exchange process while symmetric cryptography is evident when the shared secret is used in the communication process.
Diffie-Hellman Algorithm (Source)
Cryptography and Digital Signatures
Digital signatures are a way of ensuring the authenticity of electronic documents or records. By using a digital signature, a receiver verifies that the received document has not been tampered with by an unauthorised user. There is no doubt in saying that digital signatures are equivalent to handwritten signatures and stamped seals. In India, Section 3 of the Information Technology Act, 2000 recognises digital signatures and describe the process of authentication of electronic records using digital signatures as:
The authentication of the electronic record shall be effected by the use of asymmetric crypto system and hash function which envelop and transform the initial electronic record into another electronic record.
Digital signature has been defined in Section 2(1)(p) of the Information Technology Act, 2000. For digital signatures to work, public key infrastructure (PKI) is a mandatory prerequisite. Consider that there are two users: ABC and XYZ.

Digital Signature (Source)
When ABC has to send a document to XYZ, ABC will first generate a hash for this document. If the document is modified in any manner, the hash value will change. The generated hash is encrypted using ABC’s private key and the encrypted text is sent to XYZ. Upon receiving, XYZ will generate its own hash and decrypt ABC’s hash using ABC’s private key. Both these hashes are compared, and if they match, the sender is authenticated and the message has not been modified.
This article has been written by Ishika Jain, an undergraduate student at DIT University, Dehradun, during her internship with The Cyber Blog India in June/July 2020.
With contributions from Raj Pagariya.
Featured Image Credits: Background vector created by starline – www.freepik.com
