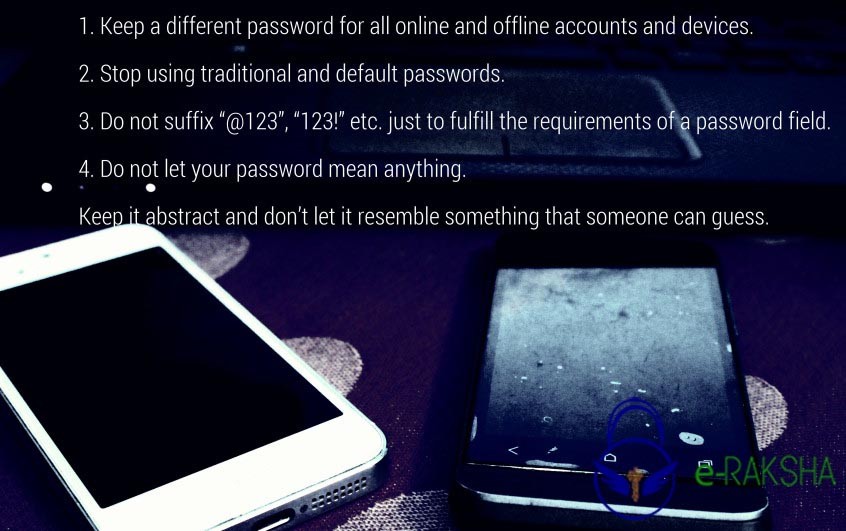
What Is Cyber Exhaust? How To Reduce It?
Everything that goes online, voluntarily or involuntarily, has some value and thus becomes a fair game for data mining. You wouldn’t even know, but the information about what you just shared on Facebook, or what answer you just upvoted … Read More